
Chameleon RAT: Unpacking the New Generation of Stealthy Android Malware
The Evolving Threat Landscape: A Deep Dive into Advanced Android RATs
The Android ecosystem, with its billions of active devices, remains a primary target for malicious actors. While users are increasingly aware of common threats like adware and ransomware, a more insidious category of malware is evolving in the shadows: the Remote Access Trojan (RAT). Recently, security researchers have been tracking a new breed of these threats, sophisticated variants that employ advanced techniques to achieve unprecedented levels of stealth and control. This article delves into this emerging threat vector, which we’ll refer to as the “Chameleon RAT,” a term encapsulating its ability to blend seamlessly into a device’s operating system, evade detection, and grant attackers near-total control over compromised Android phones. Understanding the anatomy, implications, and defense against these next-generation RATs is no longer just for security professionals; it’s essential knowledge for every Android user.
Section 1: Understanding the Chameleon RAT – More Than Just Malware
A Remote Access Trojan is a type of malware that provides an attacker with covert, administrative-level control over a victim’s device. Traditional RATs have been a staple of the cybercrime world for years, but the Chameleon RAT represents a significant leap in sophistication. Unlike its cruder predecessors that often announced their presence with poor performance or obvious malicious behavior, this new variant is defined by its stealth, persistence, and multifaceted capabilities. It operates less like a blunt instrument and more like a surgical tool for espionage and theft.
Key Characteristics of the Chameleon RAT
To appreciate the danger, it’s crucial to understand what sets this new generation of malware apart. These are not single-function threats; they are comprehensive surveillance and attack platforms.
- Advanced Evasion Techniques: The “Chameleon” moniker is earned through its ability to hide. It may use polymorphic code, which changes its signature with each infection to evade traditional antivirus scanners. Furthermore, it often injects itself into legitimate system processes or disguises its network traffic to look like benign data from a popular app, making it incredibly difficult for network-based firewalls to flag.
- Multi-Vector Infection: Initial infection is no longer limited to a user downloading a suspicious APK from a shady website. These RATs can be delivered through sophisticated phishing campaigns, compromised libraries within seemingly legitimate apps on official stores, or even by exploiting zero-day vulnerabilities in the Android OS or popular third-party applications.
- Dynamic Command and Control (C2): Older malware often communicated with a hardcoded server, which could be easily identified and blacklisted. Chameleon RATs use dynamic C2 infrastructure. They might leverage services like Telegram, Discord, or even public code repositories to receive commands, making their C2 channels resilient and hard to track. Some variants use Domain Generation Algorithms (DGAs) to constantly change their communication endpoints.
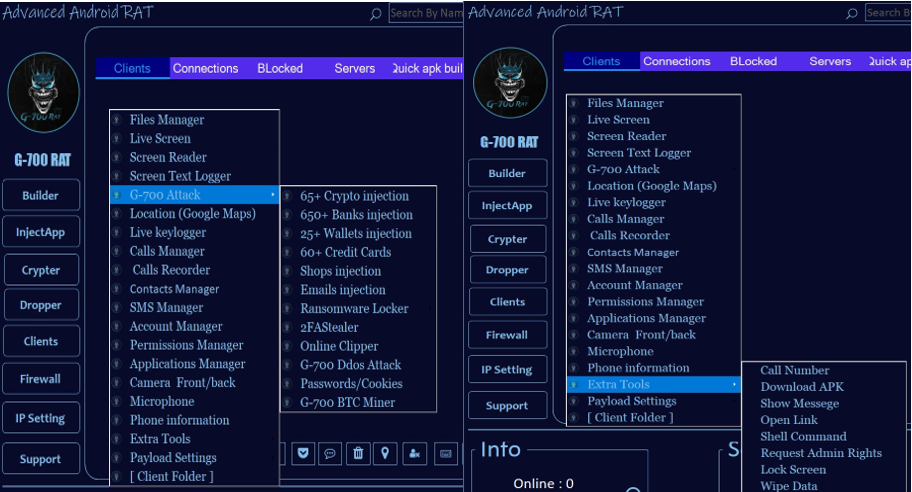
- Comprehensive Data Exfiltration: The goal is total information dominance. This includes keystroke logging, real-time screen and camera streaming, call recording, GPS location tracking, and theft of data from secure messaging apps like WhatsApp and Signal by exploiting Accessibility Services permissions.
The latest Android news from cybersecurity firms confirms this trend: attackers are moving away from noisy, widespread campaigns towards targeted, low-and-slow attacks that maximize data yield while minimizing the risk of detection. The Chameleon RAT is the perfect tool for this modern approach to mobile cybercrime.
Section 2: The Anatomy of an Attack – From Infection to Control
To truly grasp the threat, let’s break down a typical attack lifecycle involving a Chameleon RAT. This step-by-step analysis reveals the meticulous planning and technical prowess behind these campaigns, demonstrating how a user’s digital life can be completely compromised.
Phase 1: The Lure and Initial Compromise

The attack begins with social engineering. Imagine a user receives a highly convincing SMS message, seemingly from their bank or a delivery service, with a link to track a package or verify a transaction. The link leads to a professionally designed webpage that prompts them to download a “dedicated tracking app” for better service. This app is a trojanized version of a legitimate application. Upon installation, it requests a series of permissions. The most critical one is often the Accessibility Services permission, which it justifies by claiming it’s needed to “read screen content for easier form filling” or for an “enhanced user experience.”
Technical Insight: The Accessibility Services API is an incredibly powerful feature in Android, designed to assist users with disabilities. However, it has become the single most abused permission by malware authors. Once granted, it allows an app to read the text on the screen, simulate user taps, and intercept input, effectively bypassing many of the OS’s built-in security sandboxes. It’s the skeleton key for stealing credentials, 2FA codes, and chat messages.
Phase 2: Establishing Persistence and Evading Detection
Once the RAT gains initial access, its primary goal is to ensure it can survive a device reboot and remain hidden. It achieves this through several methods:
- Hiding its Icon: The malicious app’s icon will often disappear from the home screen and app drawer moments after the initial setup is complete.
- Masquerading as a System Service: The malware process will rename itself to mimic a legitimate system process, such as “com.android.system.update” or “GoogleServicesFramework,” making it difficult for a user to spot in a list of running processes.
- Delayed Execution: The RAT might lay dormant for hours or even days after installation. This “time-bomb” approach is designed to evade automated analysis tools in app stores and to break the user’s mental link between the installation of the “tracking app” and any subsequent malicious activity.
Phase 3: C2 Communication and Payload Delivery
With persistence established, the RAT “phones home” to its Command and Control server. As mentioned, it avoids standard ports and protocols. It might encrypt its communication and tunnel it through DNS queries or use a public platform like a specific Twitter feed or Pastebin page where encrypted commands are posted by the attacker. The compromised device periodically checks this source, decodes the instructions, and executes them.
The attacker can now issue a wide range of commands:
get_contacts: Exfiltrate the user’s entire contact list.start_mic_stream: Begin secretly recording audio from the microphone.show_overlay:com.example.bankingapp: When the user opens their legitimate banking app, the RAT instantly displays a pixel-perfect fake login screen (an overlay) on top of it. The user enters their credentials into the fake screen, and the data is sent directly to the attacker.get_sms_2fa: Intercept the two-factor authentication code sent via SMS to approve the fraudulent transaction.
This detailed breakdown shows how a simple click can lead to a complete and devastating compromise of one’s digital identity and financial security, all orchestrated by a silent operator thousands of miles away.
Section 3: Broader Implications for the Android Ecosystem
The rise of sophisticated threats like the Chameleon RAT has far-reaching consequences that extend beyond individual victims. It challenges the security posture of the entire Android ecosystem, from developers to enterprise IT departments.
Impact on Users and Consumer Trust
For the average user, the primary impact is a profound loss of privacy and security. The knowledge that every conversation can be recorded, every message read, and every keystroke logged creates a chilling effect. Financial losses from stolen banking credentials are the most immediate danger, but the long-term risks of identity theft, blackmail based on stolen personal data, and corporate espionage (if the device is used for work) are equally severe. This erodes user trust not just in specific apps, but in the safety of their Android gadgets as a whole.
Case Study Scenario: Consider a freelance journalist using their personal Android phone for work. They install a seemingly harmless PDF reader app from a third-party source to view a “leaked” document. The app contains a Chameleon RAT. The attacker, working for a state-sponsored group, monitors the journalist’s communications, steals drafts of sensitive stories, identifies their confidential sources through contact lists and call logs, and uses the microphone to record confidential interviews. The damage is not financial but professional and potentially life-threatening for their sources.
Challenges for App Developers
Developers are on the front lines of this battle. They face the challenge of building secure applications while being mindful that the underlying OS on a user’s device could be compromised. This means they can no longer implicitly trust the operating environment.
- Dependency Risk: An attacker might compromise a popular open-source library that thousands of apps use. By injecting malicious code into this dependency, they can effectively infect every app that includes it in their next update. Developers must now rigorously vet their software supply chain.
- Runtime Protection: Developers are increasingly turning to solutions like Runtime Application Self-Protection (RASP). RASP integrates security checks directly into an app, allowing it to detect and respond to threats in real-time, such as identifying when it’s running on a rooted device, detecting screen overlays, or noticing that a debugger is attached.
The Arms Race for Security Researchers
For the cybersecurity industry, Chameleon RATs represent a moving target. Signature-based detection is becoming obsolete. The future of mobile security lies in behavioral analysis and machine learning. On-device AI models can learn the normal behavior of a user’s phone—which apps access the network, what sensors are typically active, etc.—and flag anomalous activity that might indicate a stealthy RAT at work. This is a constant cat-and-mouse game, pushing the security community to develop more intelligent and proactive defense mechanisms.
Section 4: A Multi-Layered Defense: Best Practices and Recommendations

Protecting against a threat as sophisticated as the Chameleon RAT requires a proactive, multi-layered approach. No single solution is a silver bullet. Security is a shared responsibility, involving conscious actions from users, developers, and organizations.
Recommendations for End-Users
- App Source is Critical: Only download applications from the official Google Play Store. While not infallible, it has robust security checks that filter out the vast majority of malware. Avoid third-party app stores and sideloading APKs from unverified sources.
- Permission Scrutiny: Be a permission minimalist. Before granting a permission, ask yourself: “Does this app truly need this access to perform its core function?” A calculator app does not need access to your contacts, and a simple game does not need Accessibility Services. Deny suspicious requests.
- Keep Everything Updated: Regularly update your Android OS and all your applications. Updates frequently contain patches for security vulnerabilities that malware could otherwise exploit.
- Employ a Reputable Mobile Security App: Modern mobile security solutions from trusted vendors (e.g., Bitdefender, Malwarebytes, Norton) go beyond simple virus scanning. They offer real-time web protection, phishing alerts, and behavioral analysis to detect suspicious app activities.
- Be Skeptical of Unsolicited Messages: Treat all links in emails, SMS, and social media messages with caution. Never install software or provide credentials based on an unsolicited request.
Recommendations for Businesses and Enterprises
With BYOD (Bring Your Own Device) policies, the line between personal and corporate Android phones is blurred. A compromised personal device can become a gateway into the corporate network.
- Mobile Device Management (MDM): MDM solutions allow organizations to enforce security policies on employee devices, such as mandating screen locks, encrypting data, and creating a separate, secure work profile for corporate apps and data.
- Mobile Threat Defense (MTD): MTD solutions are the enterprise equivalent of a consumer security app but with more advanced capabilities. They can detect sophisticated threats like RATs, phishing attacks, and network-level exploits, and can automatically quarantine a device if it becomes compromised.
- Employee Education: The human element is often the weakest link. Regular training on mobile security best practices and how to recognize phishing attempts is one of the most effective defenses.
Conclusion: Vigilance in a Connected World
The emergence of advanced malware like the Chameleon RAT is a stark reminder that the mobile threat landscape is constantly evolving. These stealthy, powerful tools for espionage and theft pose a significant risk to the privacy, finances, and security of every Android user. However, succumbing to fear is not the answer. The solution lies in a combination of awareness, technology, and diligent security hygiene. By understanding the tactics used by attackers, scrutinizing app permissions, maintaining updated software, and leveraging modern security tools, users can significantly harden their devices against attack. For developers and businesses, the challenge is to build more resilient applications and enforce robust security policies. In this ongoing digital arms race, vigilance and proactive defense remain our most powerful weapons.



