The Android Update Cliff: What to Do When Your Phone Stops Getting Security Patches
The Unseen Expiration Date on Your Android Phone
In the fast-paced world of technology, we often focus on the latest features, the brightest screens, and the most powerful processors. We celebrate the launch of new Android phones and eagerly await the next big innovation. However, every device, no matter how advanced at its debut, has an unseen expiration date. This isn’t about physical wear and tear, but something far more critical: the end of software support. When a manufacturer decides a device has reached its “end-of-life” (EOL), it stops receiving crucial security patches and operating system upgrades. This transition from a secure, modern gadget to a vulnerable piece of hardware can happen silently, leaving millions of users unknowingly exposed. Understanding this lifecycle is no longer just for tech enthusiasts; it’s a fundamental aspect of digital security for every Android user. This article delves into why these updates are non-negotiable, the tangible risks of using an unsupported device, and what practical steps you can take when your trusted phone is finally put out to pasture.
Understanding the Android Support Lifecycle
The journey of an Android device from a factory to your pocket is just the beginning. Its true value and safety are maintained through a continuous stream of software updates. However, this support is finite, and knowing its limits is the first step toward protecting yourself.
The Manufacturer’s Promise: How Long is “Long Enough”?
When you purchase a new Android phone, the manufacturer makes an implicit or explicit promise of software support. For years, this was a murky area, with many devices receiving only one or two major OS updates and sporadic security patches. Thankfully, the industry has improved. The latest Android news is often dominated by manufacturers competing on support longevity.
- Google: As the creator of Android, Google sets the gold standard. For its Pixel 8 series and newer devices, it promises an unprecedented seven years of both OS and security updates.
- Samsung: A market leader, Samsung has committed to four generations of OS upgrades and five years of security updates for its flagship Galaxy S series (S21 and newer), Z series, and select A series devices. This policy is a significant reason for their continued popularity.
- Other Manufacturers: Brands like OnePlus, Xiaomi, and others typically offer policies ranging from two to four years of updates, though this can vary significantly between flagship and budget models.
This commitment is a crucial purchasing factor. A phone with a longer support window offers better long-term value and security, even if its initial cost is higher.
What “End-of-Life” (EOL) Actually Means
A device reaching its EOL isn’t just about missing out on the latest Android version with its fancy new features. The more critical cessation is that of security updates. Let’s break it down:
- OS Upgrades: These are the major version changes (e.g., from Android 13 to Android 14). They bring new features, user interface redesigns, and underlying system improvements. Missing these is an inconvenience.
- Security Patches: These are smaller, more frequent updates released by Google and device manufacturers monthly or quarterly. They don’t add features; instead, they fix newly discovered vulnerabilities in the Android operating system and device-specific software. Missing these is a critical security risk.
When a phone is declared EOL, it stops receiving these security patches. It becomes a static target, frozen in time with all its known (and yet-to-be-discovered) flaws, while hackers and malware creators continue to evolve their methods.
The High Stakes of an Unpatched Device: A Security Breakdown
Using a phone that no longer receives security updates is akin to living in a house where you’ve stopped locking the doors. You might be fine for a while, but you are willingly accepting a massive, unnecessary risk. The threats are not theoretical; they are active and constantly evolving.
Vulnerabilities: The Open Doors for Attackers
Software is incredibly complex, and flaws are inevitable. These flaws, or vulnerabilities, can be exploited by malicious actors. Security researchers and hackers are in a constant race to find them. When a “good guy” finds one, they report it to Google or the manufacturer, who then create a patch to fix it. This fix is then distributed via a security update.
For an EOL device, this entire protective cycle breaks down. A vulnerability discovered in Android’s code today could affect a phone that is five years old. While supported phones get the patch, the EOL device remains permanently vulnerable. Attackers know this and specifically target older, unpatched devices because they represent easy targets. A simple action like visiting a compromised website, opening a malicious PDF, or even connecting to a rogue Wi-Fi network could be enough for an attacker to gain control of your device.
Real-World Scenarios and Consequences
What can an attacker do with an exploited, unpatched phone? The possibilities are frightening and have tangible consequences for your privacy and finances.
- Data Theft: Attackers can access your personal photos, contacts, emails, and private messages. This information can be used for identity theft, blackmail, or sold on the dark web.
- Financial Fraud: Malware can capture your banking app credentials, credit card details, and other financial information, leading to drained bank accounts and fraudulent charges.
- Spyware and Surveillance: An attacker could activate your phone’s microphone and camera without your knowledge, turning your most personal device into a surveillance tool against you.
- Ransomware: Your device’s files could be encrypted, with attackers demanding a ransom payment to restore your access to your own photos and documents.
A prime example is the “Stagefright” vulnerability discovered years ago, which could compromise a phone with a single specially crafted multimedia message. While patched on supported devices, millions of older Android gadgets remained vulnerable indefinitely.
The Slow Decline: Beyond Security Risks
While security is the most alarming consequence of a device reaching its EOL, the user experience also degrades significantly over time, making the device increasingly frustrating to use.
The App Compatibility Wall
App developers continuously update their applications to leverage new features and security protocols available in the latest versions of Android. As time goes on, they will inevitably raise the minimum required Android version for their app to function. At first, you might not be able to update a few apps. Eventually, critical applications like your banking app, favorite social media platform, or workplace communication tool will simply stop working or refuse to install from the Google Play Store, citing an “incompatible” operating system. This effectively bricks the core functionality of a modern smartphone.

Lingering Bugs and Performance Decay
Software updates don’t just add features and patch security holes; they also fix bugs and optimize performance. An EOL phone is stuck with any bugs it had on its last day of support. A battery-draining glitch, a Wi-Fi connectivity issue, or a camera app that randomly crashes will never be fixed through an official update. The device’s performance will feel increasingly sluggish compared to modern software, with no hope of official optimization.
Diminished Resale and Trade-In Value
The market for used Android phones is savvy. A device’s software support status is a major factor in determining its value. A phone that no longer receives security updates has a drastically lower resale or trade-in value than a comparable model that is still supported. Trying to sell an EOL device means competing with a flood of similar, unsupported gadgets, all of which are considered a security risk by knowledgeable buyers.
Your Action Plan: Navigating a Device’s End-of-Life
Discovering your phone is, or soon will be, unsupported can be disheartening. However, you have several options and strategies to manage the situation effectively and safely.
Step 1: Assess Your Situation
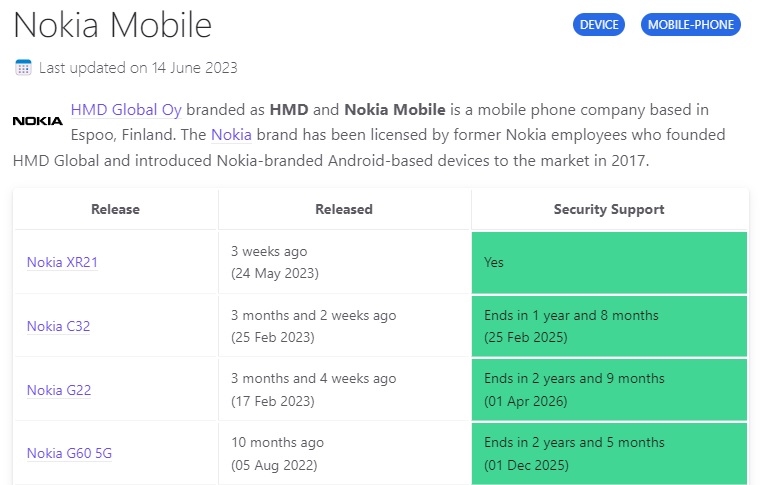
First, confirm your device’s status. You can usually find this information by searching online for “[Your Phone Model] update schedule” or checking the manufacturer’s official support website. Once confirmed, consider your usage:
- High-Risk User: Do you use your phone for banking, work emails, storing sensitive documents, or mobile payments? If so, the risk of using an unsupported device is unacceptably high. Upgrading should be your top priority.
- Low-Risk User: Do you use your phone primarily for calls, texts, and maybe some light browsing on non-sensitive sites? While still risky, you might have a bit more leeway, but you must implement strict safety measures.
Step 2: Best Practices for Using an EOL Phone (Short-Term Only)
If you absolutely cannot upgrade immediately, you must treat your device as compromised and take defensive measures. This is a temporary stopgap, not a long-term solution.
- Avoid Sensitive Data: Stop using the device for any banking, financial transactions, or accessing confidential work or personal information.
- Stick to the Play Store: Do not sideload applications (install APKs) from unknown sources. The Google Play Store has built-in security (Play Protect), which is your best line of defense.
- Be Wary of Public Wi-Fi: Avoid unsecured public Wi-Fi networks. If you must use one, use a reputable VPN to encrypt your traffic.
- Scrutinize Every Link and Message: Be hyper-vigilant about phishing attempts. Do not click on suspicious links in emails, texts, or social media messages.
Step 3: Plan Your Upgrade
For the vast majority of users, the only truly safe and practical solution is to upgrade to a new, supported device. When choosing your next phone, make the manufacturer’s software update policy a primary consideration. A phone that costs slightly more but offers five to seven years of security updates provides far better value and peace of mind than a cheaper device that will be abandoned in two years. This forward-thinking approach is the cornerstone of responsible tech ownership in today’s digital landscape.
Conclusion: Proactive Security in a Disposable World
The lifecycle of our Android gadgets is a critical aspect of our digital lives that often goes overlooked until it’s too late. The end of software support is not a minor inconvenience; it is a definitive moment when a device transitions from a trusted companion to a significant security liability. The absence of security patches leaves the door wide open to data theft, financial fraud, and privacy invasions. While the gradual decay of app compatibility and performance further erodes its utility, the security implications remain the paramount concern. As consumers, our best defense is awareness and proactivity. By understanding the update policies of different manufacturers, making support longevity a key factor in our purchasing decisions, and planning to retire devices once they cross the end-of-life threshold, we can ensure our most personal technology remains a tool for empowerment, not a vector for risk.