Android for Enterprise: More Than Just an OS, It’s a Business Ecosystem
The Unseen Powerhouse: How Android Quietly Conquered the Enterprise
When you hear the word “Android,” your mind might jump to the latest flagship smartphone, a new foldable gadget, or the vast universe of apps on the Google Play Store. For years, Android has been the undisputed king of the consumer mobile market. However, a quieter, more profound revolution has been taking place behind the scenes. The same operating system that powers your personal device has evolved into a sophisticated, secure, and incredibly versatile platform for business and enterprise. This isn’t just about checking emails on the go; it’s about transforming entire industries, from the warehouse floor to the corporate boardroom.
Forget the outdated narratives of fragmentation and security risks. Today’s Android for Enterprise is a hardened, centrally managed ecosystem designed to meet the rigorous demands of modern business. It offers a level of choice and flexibility that is simply unmatched, empowering organizations to deploy everything from rugged Android Gadgets in the field to sleek, powerful Android Phones for their executive teams. This article delves into the world of Android in the enterprise, moving beyond the technical jargon to explore the practical features, real-world applications, and strategic advantages that are making it the go-to choice for businesses worldwide. We’ll explore the latest in Android News for business and how this dynamic platform is shaping the future of work.
Section 1: The Evolution of Android in Business: From Wild West to Walled Garden
The journey of Android into the corporate world is a story of remarkable transformation. What began as a consumer-centric, open-source project has matured into a highly structured and secure enterprise-grade platform. Understanding this evolution is key to appreciating the power it holds for businesses today.
From Fragmentation to a Unified Framework
In its early days, Android’s “openness” was both a blessing and a curse for businesses. While it spurred innovation, it also led to fragmentation—a wild landscape of different OS versions, manufacturer skins, and inconsistent security patching. IT departments were understandably wary, struggling to manage and secure a diverse and unpredictable fleet of devices. This perception began to shift dramatically with the introduction of “Android for Work” in 2014, which later evolved into the comprehensive Android Enterprise framework we know today. Google created a standardized set of APIs and features that device manufacturers and Enterprise Mobility Management (EMM) providers must adhere to. This created a “walled garden” of security and manageability within the open Android ecosystem, offering businesses the best of both worlds: choice and control.
The Core Pillars of Android Enterprise
Android Enterprise isn’t a single product but a framework built on several key management models, allowing businesses to tailor their approach to specific needs:
- Work Profile (BYOD): This is the solution for the “Bring Your Own Device” world. It creates a secure, encrypted container on an employee’s personal phone. Inside this container live all the work apps and data, completely separate from the employee’s personal apps and photos. IT manages the work profile, but has no visibility or control over the personal side of the device.
- Fully Managed Device (COBO): This is for company-owned devices (“Corporate Owned, Business Only”). The organization has full control over the entire device, dictating which apps can be installed, enforcing strict security policies, and configuring every setting. This is ideal for roles handling highly sensitive data.
- Dedicated Device (COSU): Often called “kiosk mode,” this model locks down a device to a single app or a small set of apps. Think of the point-of-sale system at your local coffee shop, a self-service check-in tablet at a hotel, or a price scanner in a retail store. These are often purpose-built Android Gadgets designed for a specific task.
Why Hardware Diversity is a Business Superpower
One of Android’s most significant enterprise advantages is the sheer breadth of available hardware. Unlike a one-size-fits-all approach, businesses can choose the perfect device for any job. A logistics company can equip its warehouse staff with rugged, barcode-scanning devices from Zebra. A healthcare provider can use specialized tablets for patient charting. A sales team can be equipped with the latest Samsung Galaxy foldable phone for impressive client presentations. This diversity in Android Phones and gadgets means businesses aren’t forced to compromise, finding hardware that perfectly matches the function, environment, and budget of any role within the organization.
Section 2: Unlocking Productivity: Key Features in Real-World Scenarios
Theory is one thing, but the true value of Android Enterprise is revealed in its practical application. These features are not just about locking down devices; they are about enabling employees to be more productive, flexible, and secure, no matter where they work.
The Work Profile: A Sales Executive’s Best Friend
Imagine a top sales executive, Sarah. She uses her personal Google Pixel 8 Pro for everything. With a Work Profile, her phone has two distinct personalities. On the personal side, she has her family photos, social media, and streaming apps. But when she taps on an app with a small briefcase icon—like her work email, Salesforce, or Slack—she enters the secure work container. This data is encrypted and managed by her company’s IT department. If Sarah leaves the company, IT can remotely wipe the entire work profile in seconds, leaving her personal data completely untouched. This provides a seamless experience for Sarah, who doesn’t have to carry two phones, and complete peace of mind for her company, which knows its sensitive client data is protected.
Fully Managed Devices: Securing a Financial Firm
Now consider a financial services firm. The risk of a data breach is catastrophic. The firm issues fully managed Samsung Galaxy S24 devices to its financial analysts. These Android Phones are corporate-owned and completely locked down. The IT admin uses a platform like Microsoft Intune to enforce policies: the USB port is disabled for data transfer, the camera might be deactivated, and only a pre-approved list of applications from the Managed Google Play Store can be installed. The latest Android News on security patches is pushed to these devices automatically, ensuring they are always protected against the latest threats. This level of granular control is essential for industries with strict compliance and regulatory requirements.
Dedicated Devices: Streamlining Retail Operations
Walk into a modern big-box store, and you’ll see dedicated Android Gadgets everywhere. An employee uses a handheld scanner to check inventory levels in an aisle. A customer uses a fixed tablet to look up product information. At checkout, the cashier is using an Android-based POS system. These are all examples of dedicated devices. They are locked into a single-purpose mode, making them incredibly easy to use for employees and customers alike. The underlying Android OS provides a familiar, stable, and cost-effective platform for developers to build these custom solutions, a task that would be far more complex and expensive on a proprietary operating system.
Section 3: The Ecosystem at Work: Security, Management, and Deployment
The power of Android in the enterprise lies not just in the devices themselves, but in the robust ecosystem that supports them. This includes multi-layered security, powerful management tools, and streamlined deployment processes that save IT departments countless hours.
Fort Knox Security: A Multi-Layered Defense
The old myth of Android being insecure is just that—a myth. Modern Android is built with security at its core, featuring multiple layers of protection:
- Hardware-Level Security: Many modern Android Phones, like Google’s Pixel line with its Titan M2 chip, have dedicated hardware security modules that protect the integrity of the operating system and safeguard sensitive data like encryption keys.
- OS-Level Protections: Features like mandatory file-based encryption, sandboxing that isolates apps from each other, and verified boot ensure the device hasn’t been tampered with.
- Google Play Protect: This service continuously scans billions of apps, both on and off the Play Store, to protect devices from malware and other harmful software.
- Consistent Security Updates: Google and its partners release monthly security patches. Innovations like Project Mainline, often highlighted in Android News, allow Google to deliver critical security updates directly through the Play Store, bypassing slower carrier or manufacturer update cycles.
The Conductor’s Baton: Enterprise Mobility Management (EMM)
An Enterprise Mobility Management (or Unified Endpoint Management – UEM) platform is the central nervous system for a company’s mobile fleet. Solutions like VMware Workspace ONE, SOTI, or Microsoft Intune provide IT administrators with a single web-based console to manage every Android device in the organization. From this dashboard, they can deploy applications silently, enforce password policies, configure Wi-Fi and VPN settings, locate lost devices, and remotely wipe them if they are stolen. This centralized control is what makes managing thousands of devices feasible, turning a potential IT nightmare into a streamlined, efficient operation.
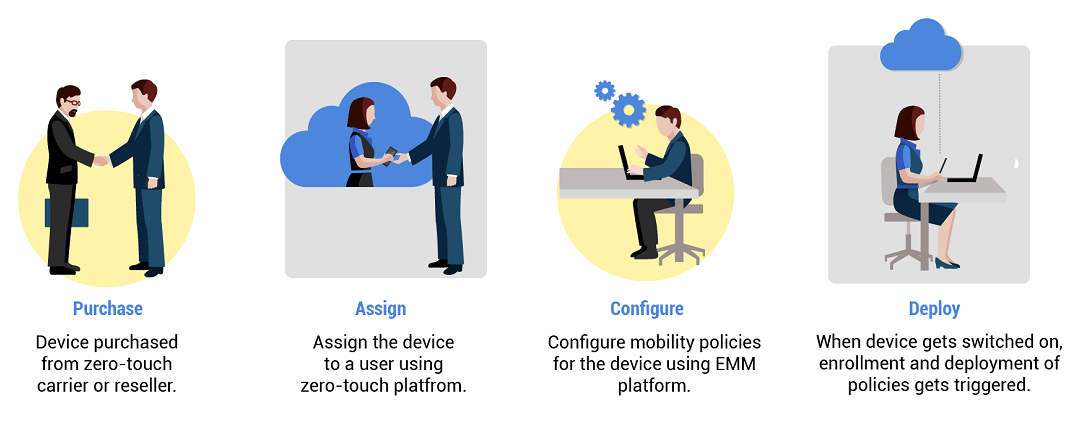
Zero-Touch Enrollment: The “Magic” of Mass Deployment
One of the most powerful features for large-scale deployments is Zero-Touch Enrollment. Imagine a company needs to deploy 1,000 new devices to its field service team. In the past, this meant an IT technician would have to manually unbox and configure every single phone—a monumental task. With Zero-Touch, the company registers the device serial numbers with a reseller. When an employee receives their new phone and turns it on for the first time, the device automatically connects to the internet, recognizes it belongs to the company, and downloads the EMM client and all the required configurations, apps, and policies. The device is ready for work in minutes, right out of the box, with zero IT intervention required. This feature dramatically reduces deployment time and costs while ensuring a consistent and secure setup for every user.
Section 4: Making the Right Choice: Best Practices and Recommendations
Successfully integrating Android into your business requires a strategic approach. Choosing the right hardware, management model, and avoiding common pitfalls are crucial for a successful and secure mobile strategy.
Choose Your Fleet Wisely: Android Enterprise Recommended
With thousands of Android models on the market, how do you choose? Google has simplified this with the Android Enterprise Recommended program. This is a curated list of devices that Google has verified meet strict enterprise-grade requirements for hardware, software, security updates, and user experience. By choosing a device from this list—which includes models from top manufacturers like Samsung, Google, Nokia, and others—businesses can be confident they are getting a device that is built for business, guaranteed to receive timely security updates, and supports key features like Zero-Touch Enrollment.
BYOD vs. Corporate-Owned: A Strategic Decision
The choice between allowing employees to use their own devices (BYOD) and issuing company-owned phones is a critical one.
- BYOD (with Work Profile) is often more cost-effective and preferred by employees who don’t want to carry two devices. It’s great for roles where the primary need is access to email, calendars, and collaboration apps.
- Corporate-Owned (Fully Managed or Dedicated) offers maximum security and control. It’s the best choice for employees handling sensitive intellectual property, financial data, or for purpose-built roles using Android Gadgets. Many companies are also adopting a “COPE” (Corporate Owned, Personally Enabled) model, which provides a company phone but still allows for some personal use, offering a middle ground.
Common Pitfalls to Avoid
As you deploy your Android fleet, be mindful of these common mistakes:
- Neglecting Management: Trying to manage devices without a proper EMM solution is inefficient and insecure.
- Wrong Device for the Job: Don’t give a fragile, consumer-grade smartphone to a construction worker. Invest in rugged devices for harsh environments.
- Poor Communication: When deploying Work Profiles, clearly communicate to employees what IT can and cannot see on their personal devices to build trust and encourage adoption.
Conclusion: Android is Ready for Business
The Android of today is a far cry from its early, untamed origins. It has matured into a secure, manageable, and extraordinarily flexible enterprise platform. Through the robust Android Enterprise framework, it offers tailored solutions for virtually any business need, from securing employee-owned phones to deploying fleets of single-purpose gadgets. The vast choice in hardware, combined with powerful management tools and a multi-layered security architecture, provides a compelling value proposition for any organization looking to modernize its mobile strategy.
By leveraging features like the Work Profile, Zero-Touch Enrollment, and the Android Enterprise Recommended program, businesses can empower their workforce, streamline operations, and protect their data with confidence. As the world of work becomes increasingly mobile, the ecosystem of Android Phones and Android Gadgets is no longer just a consumer phenomenon—it’s a critical engine of business productivity and innovation.