Your Digital Fortress: A Deep Dive into Modern Android Security & Privacy
Your Digital Fortress: A Deep Dive into Modern Android Security & Privacy
In an age where our lives are intricately woven into the digital fabric, the device in our pocket is more than just a phone—it’s a vault. It holds our conversations, financial details, photos, and location history. This makes the security and privacy of our Android phones a topic of paramount importance, one that frequently dominates headlines in Android News. Many users, however, feel a sense of digital anxiety, viewing security as a complex, impenetrable subject best left to experts. The reality is quite different. Modern Android has evolved into a sophisticated, user-centric fortress, equipping you with powerful, intuitive tools to protect your digital life. This article will demystify those features, moving beyond technical jargon to provide a comprehensive guide on how to take control of your privacy, understand the built-in protections, and make informed decisions about your favorite Android gadgets.
The Silent Guardian: Understanding Android’s Built-in Defenses
Before you even touch a single setting, your Android phone is already working overtime to protect you. Google has built a multi-layered security architecture directly into the operating system. These are the “silent guardians” that form the foundation of your device’s safety, operating seamlessly in the background. Understanding them is the first step to appreciating the depth of Android’s commitment to security.
Google Play Protect: The Bouncer at the App Door
Think of Google Play Protect as the vigilant bouncer for your phone. It’s a suite of security services that continuously works to keep your device, data, and apps safe. Its primary job is to scan apps on the Google Play Store before you download them, checking for malware and other malicious code. But its work doesn’t stop there. Play Protect also periodically scans the existing apps on your phone, whether you downloaded them from the Play Store or not. According to Google, it scans over 125 billion apps every single day across the Android ecosystem. If it finds a potentially harmful application (PHA), it will either notify you to uninstall it or, in severe cases, remove it automatically. This is your first and most crucial line of defense against the vast majority of mobile threats.
Project Mainline & Security Updates: Patching the Armor
In the past, critical security updates were often bundled with major OS updates, which could be delayed by carriers and manufacturers. This left devices vulnerable for extended periods. The latest Android News often highlights the importance of timely updates, and Google’s Project Mainline (officially known as Google Play system updates) is the solution. It modularizes core components of the Android OS, allowing Google to push critical security and privacy fixes directly to your device via the Play Store, just like an app update. This bypasses the slower manufacturer/carrier update cycle. For users, this means your phone’s digital armor is patched faster and more consistently, protecting you from newly discovered vulnerabilities without waiting for a full OS upgrade.
Sandboxing and Encryption: Building Digital Walls
At its core, Android is designed around a principle of containment called “sandboxing.” Each app on your phone runs in its own isolated space, or sandbox. This means an app can only access its own files and data; it cannot snoop on the data of other apps. For example, a simple game app is walled off from your banking app’s data. This fundamental architecture severely limits the damage a rogue app can cause. Furthermore, modern Android phones come with file-based encryption enabled by default. This means all your personal data on the device is scrambled and can only be unlocked with your PIN, pattern, or biometric authentication. Even if someone physically stole your phone, they wouldn’t be able to access your photos, messages, or files without your credentials.
You’re in Control: Mastering Your Privacy Dashboard and Permissions
While Android’s built-in defenses are robust, the most powerful security tool is an informed user. Recent Android versions (Android 12 and later) have introduced a suite of transparent, easy-to-use privacy controls that put you firmly in the driver’s seat. It’s time to move from being a passive passenger to an active pilot of your own data.
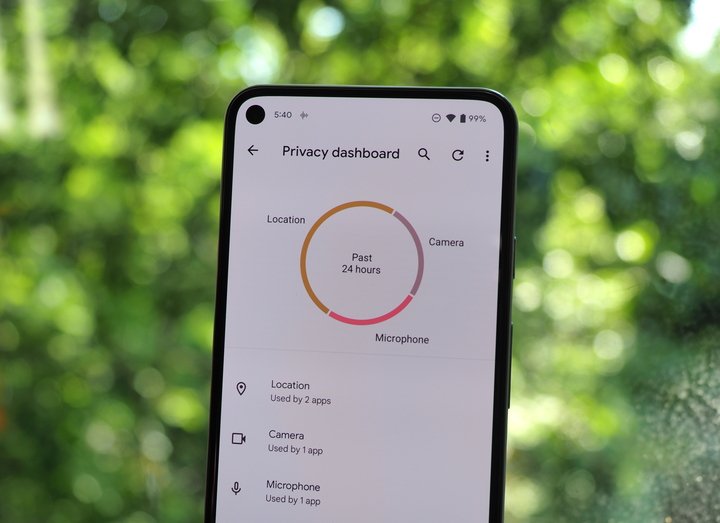
The Privacy Dashboard: Your Personal Security Log
The Privacy Dashboard is your central command for data access. Found in Settings > Security & privacy > Privacy, it provides a clear, simple timeline showing which apps have accessed sensitive permissions like your location, camera, and microphone in the last 24 hours (or 7 days on some devices).
Real-World Scenario: You notice a weather app accessed your location 50 times in the last 24 hours, even when you weren’t using it. The Privacy Dashboard highlights this. You can then tap on the location entry, select the weather app, and change its permission from “Allow all the time” to “Allow only while using the app.” This single action prevents the app from tracking you in the background while still allowing it to function when you need it. It’s an actionable insight that gives you immediate control.
Granular Permissions: The Power to Say “No” (or “Only Sometimes”)
The days of all-or-nothing permissions are over. Android now offers granular control:
- Allow only while using the app: The gold standard for most permissions like location or camera.
- Ask every time: Ideal for permissions you use infrequently, forcing an app to justify its request each time.
- Don’t allow: A clear “no” to an app’s request.
A crucial addition is the “Precise Location” toggle. A navigation app like Google Maps needs your precise location. However, a local news app only needs your general area to show relevant stories. You can grant it location access but turn off the “Use precise location” switch, giving it only an approximate idea of where you are. This is a perfect example of the principle of least privilege: give an app only the bare minimum data it needs to function.
Indicators and Quick Toggles: Real-Time Awareness
Have you ever seen a small green dot appear in the top-right corner of your screen? That’s not a glitch. It’s a privacy indicator. A green dot means an app is actively using your camera, microphone, or both. Swiping down reveals which specific app is responsible. This real-time alert system makes it impossible for an app to secretly spy on you.
Furthermore, the Quick Settings panel includes “Camera access” and “Mic access” toggles. Tapping these instantly blocks access to the camera or microphone for all apps on your phone. This is a digital kill switch, perfect for moments when you want absolute certainty that nothing is watching or listening.
Beyond the Phone: Securing Your Entire Android Ecosystem
Your digital life extends beyond a single smartphone. It encompasses a network of Android gadgets, from smartwatches and tablets to smart home devices, all connected through your Google Account. Securing this broader ecosystem requires a holistic approach, ensuring that a weak link in one area doesn’t compromise the entire chain.
Your Google Account: The Master Key to Your Kingdom
Your Google Account is the central hub of your Android experience. If it’s compromised, an attacker could gain access to your emails, photos, contacts, and even the location of your devices. The single most important step you can take to secure it is enabling Two-Factor Authentication (2FA). With 2FA, even if someone steals your password, they cannot log in without a second verification step, usually a code sent to your phone. You can check your account’s security status anytime by visiting the Google Account security checkup page. It provides a personalized, step-by-step guide to strengthening your account’s defenses.
Find My Device: Your Digital Search and Rescue
Losing a phone or tablet is stressful, but Android’s Find My Device service can be a lifesaver. It’s more than just a map; it’s a remote security tool. If you misplace a device, you can use Find My Device to:
- Locate it on a map.
- Play a sound at full volume, even if it’s on silent.
- Secure the device by remotely locking it and displaying a message on the screen (e.g., “This phone is lost, please call [your number]”).
- Erase the device as a last resort, performing a factory reset to wipe all your personal data and prevent it from falling into the wrong hands.
This service extends to compatible Android gadgets like Wear OS smartwatches, making it an essential tool for your entire device family.
The Sideloading Dilemma: A Word of Caution
One of Android’s strengths is its openness, which includes the ability to “sideload” apps by installing APK files from outside the Google Play Store. While this allows for greater flexibility, it also carries significant security risks. Apps from unofficial sources are not vetted by Google Play Protect and can easily contain malware, spyware, or other malicious code.
Best Practice: For 99% of users, it’s best to stick to the Google Play Store. If you must sideload an app, ensure it’s from a highly reputable source like the developer’s official website or a trusted repository like F-Droid. Always be cautious and understand that you are bypassing Android’s primary layer of app security.
Choosing Your Fortress: Pixel vs. Samsung and What to Look For
Not all Android phones are created equal when it comes to security. While they all share the same core Android OS, manufacturers add their own hardware, software, and, most importantly, have different update policies. Making an informed purchasing decision is a key part of your security strategy.
The Great Debate: Pixel vs. Samsung Knox
When it comes to security, two names often lead the conversation: Google’s Pixel line and Samsung’s Galaxy devices.
- Google Pixel Phones: Pixels are the benchmark for Android security. They receive security updates directly from Google on day one, ensuring they are always protected against the latest threats. They also feature dedicated security hardware, like the Titan M2 chip, which handles sensitive processes like encryption and biometric authentication in a secure, isolated environment. This hardware-level protection makes them incredibly difficult to compromise.
- Samsung Galaxy Phones (with Knox): Samsung has invested heavily in its own security platform, Samsung Knox. It’s a defense-grade security framework that is built into their devices from the chip up. Knox provides features like a Secure Folder—an encrypted space on your phone to store private files, photos, and apps—and real-time kernel protection. In recent years, Samsung has also become a leader in software support, promising up to seven years of security updates for its flagship devices, a commitment that often surpasses even Google’s.
The choice often comes down to priorities. If you value immediate updates and a pure, hardware-integrated security experience, Pixel is a top contender. If you appreciate a robust, multi-layered software platform and the longest update promise in the industry, Samsung is an excellent choice.
A Buyer’s Checklist for a Secure Android Phone
When you’re browsing the latest Android News for your next phone, keep these security factors in mind:
- Manufacturer’s Update Policy: This is the most critical factor. Look for manufacturers that promise at least 4-5 years of consistent and timely security updates.
- Dedicated Security Hardware: Look for mentions of a dedicated security chip (like Google’s Titan M or a similar Secure Element) in the phone’s specifications.
- Biometric Security: Test the fingerprint sensor and face unlock. A fast, reliable biometric system means you’re more likely to use it, keeping your phone locked and secure.
- Stock vs. Skinned Android: Phones closer to “stock” Android (like those from Google, Nokia, or Motorola) often receive updates faster than those with heavily customized software skins.
Conclusion: Security as a Partnership
The landscape of Android security is no longer a cryptic, backend affair. It has transformed into a transparent and user-empowering partnership. Google provides a powerful, multi-layered fortress with features like Google Play Protect, sandboxing, and Project Mainline. Simultaneously, it hands you the keys to the kingdom through the Privacy Dashboard, granular permissions, and real-time indicators. By understanding these built-in protections and actively managing your privacy settings, you can transform your device from a potential liability into a secure vault for your digital life. Staying informed through Android News, choosing devices from manufacturers with strong update policies, and practicing digital diligence are the pillars of modern mobile security. Your Android phone is an incredibly powerful tool; with the right knowledge, you can ensure it works for you, and only for you.