Unmasking the Watchers: How Future Android Phones Will Detect Fake Cell Towers
The Invisible Threat: A New Era of Security for Android Users
In our hyper-connected world, our smartphones are our lifelines. We rely on them for communication, navigation, finance, and entertainment, trusting the cellular networks that underpin this connectivity. However, a silent and largely invisible threat exists that can turn this trust on its head: fake cell towers. Known technically as IMSI-catchers and colloquially as “Stingrays,” these devices pose a significant risk to personal privacy and data security. For years, detecting them has been the domain of specialized equipment and highly technical experts. That is about to change. In a landmark development for mobile security, upcoming versions of the Android operating system are set to include a native feature that can detect and warn users about these malicious towers. This is major Android News, signaling a pivotal shift from passive vulnerability to proactive defense, empowering millions of users of Android phones with the knowledge they need to protect their digital lives.
This article provides a comprehensive technical deep-dive into this upcoming security feature. We will explore what IMSI-catchers are and how they work, break down the sophisticated methods Android will use to detect them, analyze the profound implications for user privacy and the surveillance landscape, and offer practical advice for users to enhance their mobile security today. This isn’t just an incremental update; it’s a fundamental enhancement to the security posture of the entire Android ecosystem.
Understanding the Threat: What Are IMSI-Catchers?
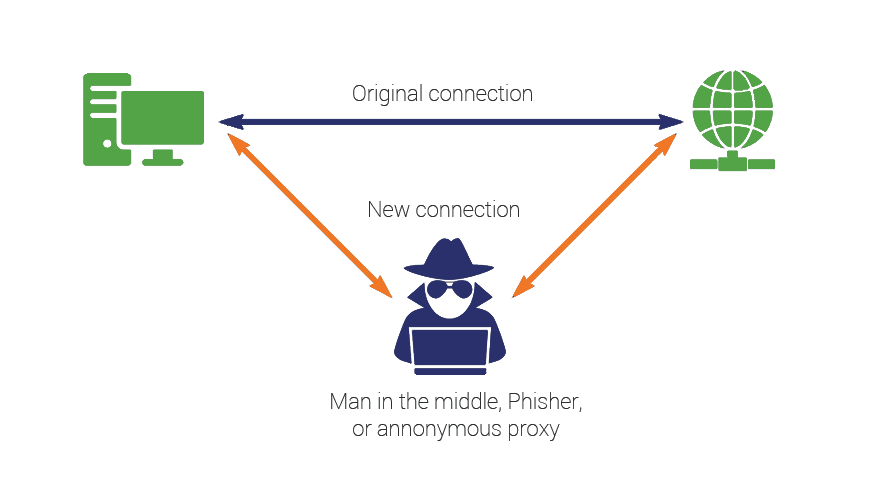
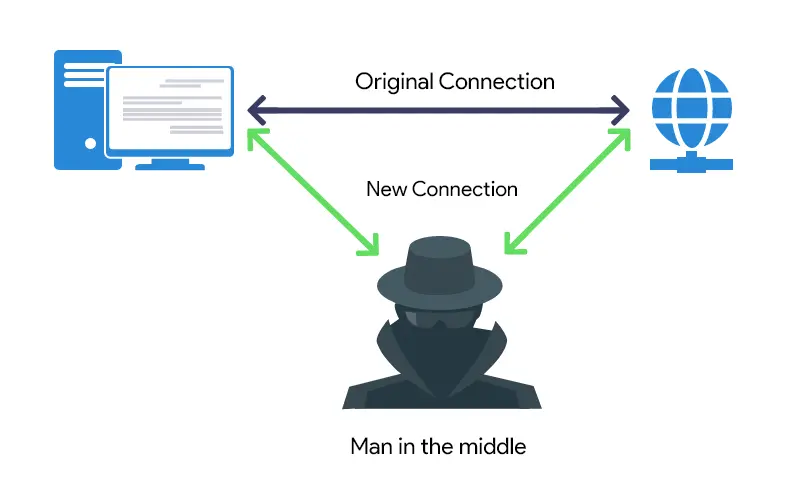
Before appreciating the solution, it’s crucial to understand the problem. IMSI-catchers are sophisticated pieces of hardware that masquerade as legitimate cell towers, tricking nearby mobile devices into connecting to them. This creates a classic “man-in-the-middle” attack, positioning the malicious actor directly between you and your mobile carrier’s network.
How a “Stingray” Attack Unfolds
The core function of an IMSI-catcher is to exploit the way cell phones are designed to seek out the strongest available signal. The device broadcasts a powerful, appealing signal that overrides the legitimate towers in the vicinity. Your phone, programmed to ensure a stable connection, automatically connects to this seemingly superior tower. Once connected, the attacker can execute several malicious actions:
- Identity Harvesting: The primary goal is often to capture a device’s International Mobile Subscriber Identity (IMSI). This unique number is tied to your SIM card and can be used to track your location and movements over time.
- Metadata Interception: The attacker can log all your call metadata—who you call, who calls you, the time and duration of calls, and your location when the calls were made.
- Traffic Interception: By forcing a connection downgrade to older, less secure network protocols like 2G (GSM), attackers can potentially intercept the content of unencrypted calls and SMS messages. While most internet data is now protected by HTTPS, any unencrypted app data or communications could be exposed.
- Denial of Service: An IMSI-catcher can be used to simply block a specific user or group of users from accessing cellular services.
Who Uses Them and Why?
While originally developed for military and intelligence applications, the technology has proliferated. Law enforcement agencies around the world use them, often without a warrant, to track suspects. However, the decreasing cost and increasing availability of the required hardware and software have put these powerful tools into the hands of malicious actors. Criminal organizations use them for industrial espionage, tracking high-value targets for theft, and perpetrating sophisticated financial fraud. This widespread availability makes the threat relevant to everyone, not just high-profile individuals.
The Current Vulnerability of Android Gadgets
Until now, the vast majority of commercial Android gadgets have been blind to this threat. The complex signaling and authentication that happens between a phone’s modem and a cell tower occurs at a very low level, far removed from the user interface and most applications. While some specialized apps exist that attempt to detect anomalies, they often require deep system access (root permissions) and have limited reliability. For the average user, there has been no built-in, trustworthy way to know if their connection has been compromised.
Android’s Countermeasure: A Technical Deep Dive
Google’s plan to combat IMSI-catchers involves deep integration between the phone’s hardware (the cellular modem) and the Android operating system. The system will be trained to identify several key red flags that are characteristic of a fake cell tower’s operation. This isn’t a single check, but a multi-faceted analysis of the cellular environment.
The Core Detection Mechanisms
The new security feature will rely on identifying anomalies that deviate from the standard, secure operating procedures of legitimate cellular networks. The OS will be listening for specific signals passed up from the modem that indicate a potential man-in-the-middle attack.
1. Identifying Null Ciphers: In a secure connection, all communication between your phone and the tower is encrypted. IMSI-catchers, particularly older or simpler models, often bypass this by instructing the phone to use a “null cipher.” This essentially means the connection has zero encryption, allowing the attacker to easily monitor traffic. The new Android feature will explicitly detect when a tower requests or forces a null cipher state, which is a massive and unambiguous red flag for a malicious actor. A legitimate network would almost never do this.
2. Detecting 2G Downgrade Attacks: Modern 4G (LTE) and 5G networks feature robust security and encryption protocols that are difficult to break in real-time. To circumvent this, many IMSI-catchers execute a “downgrade attack.” They trick the phone into believing that 4G/5G service is unavailable, forcing it to fall back to the antiquated and notoriously insecure 2G (GSM) network. The encryption used in 2G is weak and has been broken for years, making it trivial for an attacker to intercept calls and texts. Android will be able to recognize when a device is being illegitimately forced down to 2G in an area where strong 4G/5G service is known to be available, triggering an alert.
3. Verifying Network Identity and Configuration: Legitimate cell towers broadcast a rich set of information about themselves and the network they belong to, including a Mobile Country Code (MCC), Mobile Network Code (MNC), and Location Area Code (LAC). Fake towers often fail to configure this information correctly. They might omit certain parameters, use conflicting identifiers, or present a configuration that doesn’t match the phone’s known database of legitimate towers in the area. The modem can detect these inconsistencies and report them to the OS as a sign of a spoofed tower.
From Modem to User: The Alerting Pipeline
This entire process represents a significant engineering effort. The cellular modem, which operates on its own low-level firmware, must first be capable of identifying these anomalies. It then needs a secure channel to communicate this raw data to the main Android OS. The OS will then interpret this information, correlate it with other data (like known network status and location), and determine if the threat level is high enough to warrant a user notification. The final step would be a clear, unambiguous alert presented to the user, potentially with actionable advice like “Disable your cellular connection” or “Avoid sensitive communications.”
A New Era for Mobile Security: What This Means for You
The introduction of native IMSI-catcher detection in Android phones is more than just a new feature; it’s a paradigm shift in the balance of power between individuals and those who would seek to monitor them. The implications are far-reaching for privacy, security, and the surveillance industry.
Empowering the Everyday User with Actionable Intelligence
For the first time, average citizens will have a built-in tool that provides visibility into a previously invisible layer of surveillance. This transforms users from potential passive victims into informed actors. Upon receiving an alert, an individual can make a conscious decision to protect themselves. A journalist meeting a sensitive source could immediately switch to a secure Wi-Fi network. A business executive in a foreign country could refrain from making sensitive calls. A protestor could power down their device to avoid being tracked. This democratization of security knowledge is a powerful tool for personal freedom and privacy.
A Direct Challenge to Covert Surveillance Operations
The widespread deployment of this feature will significantly raise the cost and complexity of running covert surveillance operations. Law enforcement and intelligence agencies that rely on IMSI-catchers will find their targets are now alerted to their presence. This will force them to either develop far more sophisticated (and expensive) technology that can better mimic legitimate towers or to rely on more traditional, court-authorized surveillance methods. This development could bring a new level of public accountability to the use of such surveillance tools, which have often been deployed with minimal oversight.
Setting a New Baseline for the Mobile Industry
When a platform as massive as Android introduces a fundamental security feature, it sets a new standard for the entire industry. It places immense pressure on Apple to provide a similar level of transparent protection for iOS users. Furthermore, it incentivizes cellular carriers to accelerate the decommissioning of their legacy 2G networks, which are the primary enablers of the most effective IMSI-catcher attacks. This single feature could catalyze a wave of security improvements across the entire mobile ecosystem, benefiting all users in the long run.
Navigating the New Landscape: Best Practices and Limitations
While this upcoming feature is a game-changer, it’s important to have a realistic perspective on its capabilities and to continue practicing good digital hygiene. No single tool is a silver bullet for all security threats.
Recommendations and Best Practices for Today
While we await the rollout of this feature, there are steps you can take right now to protect your communications:
- Use End-to-End Encryption: For all your messaging and calling, rely on apps that use strong end-to-end encryption, such as Signal or WhatsApp. This ensures that even if your traffic is intercepted, its content remains unreadable.
- Employ a VPN: A reputable Virtual Private Network (VPN) encrypts all the internet data leaving your device. While it won’t stop IMSI-based location tracking or call metadata collection, it will protect your data traffic from being snooped on by a fake tower.
- Prefer Modern Networks: In your phone’s network settings, set the preferred network type to “5G/LTE Only” if the option is available. This can help prevent automatic downgrades to 2G, though it may cause connectivity issues in areas with poor 4G/5G coverage.
- Be Wary of Public Wi-Fi: Fake Wi-Fi hotspots are another common man-in-the-middle threat. Treat them with the same suspicion as a potential fake cell tower.
Potential Limitations and Future Challenges
It’s important to acknowledge potential limitations. The system may generate false positives in areas with misconfigured or fringe network coverage. The effectiveness will also be highly dependent on the modem chipset in your specific Android device; older or budget Android gadgets may not have the hardware support to enable this feature. Moreover, the security landscape is a constant cat-and-mouse game. As this detection becomes widespread, a new generation of more advanced IMSI-catchers will inevitably be developed to try and circumvent these new defenses.
Conclusion: A Major Leap Forward for Digital Privacy
The impending arrival of native fake cell tower detection in Android marks a pivotal moment in the history of consumer mobile security. It addresses a long-standing and serious vulnerability, pulling back the curtain on a form of covert surveillance that has operated in the shadows for far too long. By building this capability directly into the operating system, Google is democratizing security and providing hundreds of millions of users with the tools to understand and react to threats in their environment. While not an infallible solution, it represents a massive and commendable step toward rebalancing the scales of privacy. This feature is one of the most significant pieces of Android News in recent memory, promising a safer, more transparent future for users of Android phones and devices worldwide.